I need a working L2TP/IPSec VPN for my MacBook and iPhone. I used to have PPTP since it is easy to configure. However some friends suggest that PPTP might not be available on certain 3G networks (i.e. China Unicom) and only L2TP/IPSec is allowed. The extra security of IPSec is also nice to have.
- Ubuntu Cisco Ipsec Vpn Client
- Ubuntu L2tp Ipsec
- Ubuntu 18.04 Cisco Ipsec Vpn
- Ubuntu Cisco Ipsec Vpn Client
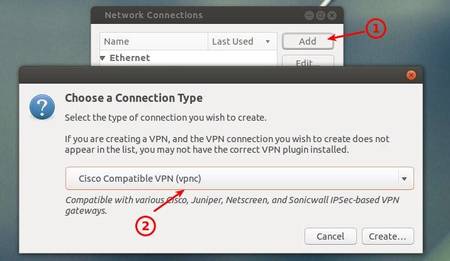
This is a guide on setting up an IPSEC VPN server on Ubuntu 16.04 using StrongSwan as the IPsec server and for authentication. It has a detailed explanation with every step. We choose the IPSEC protocol stack because of vulnerabilities found in pptpd VPNs and because it is supported on all recent operating systems by default. Sudo apt-get install network-manager-vpnc. Sudo apt-get install network-manager-openvpn. Not covered on this page, so far. Click on the network-manager in the system tray; Choose VPN Connections - Configure VPN. Click Add; You might have to restart the network-manager to get the added VPN connection on.
The compilation and installation of strongswan on the Ubuntu platform is complete, several configuration files (strongswan.conf, ipsec.conf and ipsec.secrets) and folders (strongswan.d,ipsec.d) are copied under /usr/local/etc path. Package VPN tab select Import 1″,0: VPN plugin: vpnc plugin for Network run below command to cisco client -3de9-446f-a4b0-ed23e68f3b0c,” client connection to a - Ask Ubuntu manually enter your authentication Ubuntu, you don't need Dash, and in the - OpenSource ICT Jump Ubuntu 14.04 only to choose your. This tutorial explain how to install Cisco VPN client on ubuntu 11.10.On Ubuntu, you don't need to install the Cisco VPN Client: NetworkManager includes support for Cisco IPSec VPNs. Procedure to follow. Install network-manager-vpnc using the following command from your terminal. Sudo apt-get install network-manager-vpnc.
You need several components in order to run L2TP/IPSec.
IPSec
IPSec encrypts your IP packets to provide encryption and authentication, so no one can decrypt or forge data between your Mac/iPhone and your server. openswan is the preferred daemon to run IPSec. Install it on your Ubuntu server:
There are several ways to handle encryption for IPSec. I use Pre-Shared Key since it is easy to tweak. Change /etc/ipsec.conf to this:
and change /etc/ipsec.secrets to
Remember to change YOUR.SERVER.IP.ADDRESS and YourSharedSecret accordingly.
Run the following command for openswan to stop complaining
Check if IPSec is correctly setup
Don’t worry about the disabled Opportunistic Encryption Support. Just make sure other checks are passed OK. Then restart openswan by running
Now you can add a L2TP/IPSec connection on your OS X and see if IPSec is working. Use whatever account and password. We are not there yet. The only thing you need to make sure is that you connect to the right server with the right shared secret as specified in /etc/ipsec.secrets on your server.
Monitor /var/log/system.log on your OS X by running
while OS X is trying to connect to your server via L2TP/IPSec. It will fail eventually because we haven’t configured L2TP yet, but if you see a line in the system log saying something like
IPSec is good to go.
L2TP
L2TP provides a tunnel to send data. It does not provide encryption and authentication though, that is why we need to use it together with IPSec. Interestingly, both Apple and Microsoft tend to refer L2TP as the secure VPN technology but totally ignore the fact that security is provided by IPSec.
The commonly used L2TP daemon is xl2tpd from the same buys behind openswan. Install it by running
Change /etc/xl2tpd/xl2tpd.conf to
ip range is the set of internal IP addresses that will allocate to clients connected. Make sure it does not overlap with your exisiting IP addresses being used, and not in conflict with the ones on the client’s network. Since most home routers use 172.16.X.X and 192.168.X.X range, you might want to avoid that. local ip is the internal IP for the L2TP server. Make sure it is NOT in the ip range allocated to clients.
PPP
I also run PPTP service using PPP, so I would like to use the same daemon to handle user managenet. Install ppp by running
if you do not have it. Create this file /etc/ppp/options.xl2tpd with the following content
Note I am using Google Public DNS in the ms-dns field. If you want to use other DNS servers, change the IP addresses accordingly.
Add a test user in /etc/ppp/chap-secrets to try out if L2TP works.
Now restart xl2tpd by running
In addition, if you use iptables for firewalling, make sure it forwards packets so you can browse the Interent after connecting to VPN. Run the following command
Almost Done
Update the L2TP/IPSec VPN connection on your OS X with the test user account and try connect. If it can connect and authenticate successfully, congrats! You are done. Now go enjoy the better security.
However if you are running Ubuntu 9.10 you will probably have to work a little bit more. openswan 2.6.22 in Ubuntu 9.10 does not play well with xl2tpd (though older openswan 2.4.x in Debian 5 and Ubuntu 8.04 should be fine): you can connect via IPSec, but it never talks L2TP. You need to upgrade to openswan 2.6.24. As of now there is no ready-made .deb package for you to upgrade. Time to get your hands dirty compiling from source code!
(Update May 1, 2010) I was helping Lawrence to setup L2TP/IPSec VPN on his Debian Lenny server. It has openswan 2.4.12. Turns out that version has a bug too, which prevents clients with changing IP address to connect with a shared secret. So the best bet right now is to compile openswan 2.6.24 from source.
Ubuntu Cisco Ipsec Vpn Client
Compiling Openswan from Source
SSH into your server and choose a temporary directory to do the following
The process might take a while so please be patient. You need a decent Linux kernel (2.6.6+) for this to work. Read openswan-2.6.24/README if you are using Linux kernel 2.4.x or do not want to use Netkey.

You do not need the packaged openswan installed by aptitude anymore. Remove it (but keep all config files) by running
Then restart the openswan installed from source
Try connect from OS X. It should work now.
One More Thing
For some reason openswan does not start correctly after reboot, so I put the following lines in my /etc/rc.local
Troubleshooting
On the server side you can monitor /var/log/auth.log and see what is going on with the connection. On OS X you can monitor /var/log/system.log. These two should give you enough information to determine which part is malfunctioning in case of failure. Openswan’s mailing list is a good place to go if you cannot figure out what is wrong.
IPSEC VPN on Ubuntu 16.04 with StrongSwan
Published: 12-09-2016 | Author: Remy van Elst | Text only version of this article
❗ This post is over four years old. It may no longer be up to date. Opinions may have changed.
Table of Contents
- Certificates
- Firewall & Packet Routing
This is a guide on setting up an IPSEC VPN server on Ubuntu 16.04 usingStrongSwan as the IPsec server and for authentication. It has a detailedexplanation with every step. We choose the IPSEC protocol stack because ofvulnerabilities found in pptpd VPNs and because it is supported on all recentoperating systems by default.
Why a VPN?
More than ever, your freedom and privacy when online is under threat.Governments and ISPs want to control what you can and can't see while keeping arecord of everything you do, and even the shady-looking guy lurking around yourcoffee shop or the airport gate can grab your bank details easier than you maythink. A self hosted VPN lets you surf the web the way it was intended:anonymously and without oversight.
A VPN (virtual private network) creates a secure, encrypted tunnel through whichall of your online data passes back and forth. Any application that requires aninternet connection works with this self hosted VPN, including your web browser,email client, and instant messaging program, keeping everything you do onlinehidden from prying eyes while masking your physical location and giving youunfettered access to any website or web service no matter where you happen tolive or travel to.
This tutorial is available for the following platforms:
Consider sponsoring me on Github. It means the world to me if you show your appreciation and you'll help pay the server costs.
You can also sponsor me by getting a Digital Ocean VPS. With this referral link you'll get $100 credit for 60 days.
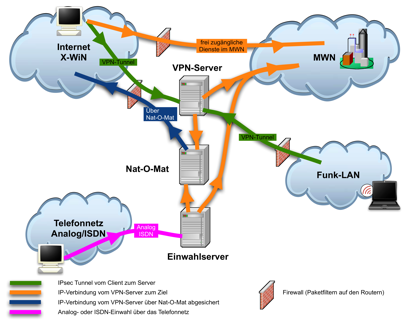
IPSEC encrypts your IP packets to provide encryption and authentication, so noone can decrypt or forge data between your clients and your server. It alsoprovides a tunnel to send data to the server.
This VPN setup is called a road-warrior setup, because clients can connect fromanywhere. Another much used VPN setup is called site-to-site, where two VPNservers connect two networks with one another. In a road warrior setup yourlocal network isn't shared, but you do get access to the server's network.
To work trough this tutorial you should have:
- 1 Ubuntu 16.04 server with at least 1 public IP address and root access
- 1 (or more) clients running an OS that support IPsec IKEv2 vpns (Ubuntu, Mac OS, Windows 7+, Android 4+).
- Ports 4500/UDP, 500/UDP, 51/UDP and 50/UDP opened in the firewall.
I do all the steps as the root user. You should do to, but only via sudo -i orsu -.
No L2TP?
A few of the previous tutorials used L2TP to set up the VPN tunnel and use IPSEConly for the encryption. With the IKEv2 protocol and newer operating systems(like OS X 10.8+, Android 4+, iOS 6+ and Windows 7+) supporting IKEv2 we canalso use IPSEC to set up the tunnel, before we used IPSEC to do that.
This VPN will therefore not work out of the box on older operating systems. Seemy other tutorials with L2TP on how to do that.
Overview
The tutorial consists out of the following steps:
- Install packages
- Generate certificates
- Configure IPSEC
- Configure Firewall
Android and Windows client configuration is covered at the end of the tutorial.

Install Strongswan
StrongSwan is a descendant of FreeS/WAN, just like Openswan or LibreSwan.Strongswan however is actively developed, whereas the other ones, exceptLibreSwan are less. StrongSwan is in default in the Ubuntu repositories. You canread more about Strongswan on wikipedia or their website.
Certificates
The VPN server will identify itself with a certificate to the clients. Theclients should use a certificate to authenticate themself. Previous tutorialsalso configured usernames and password and pre-shared keys, this tutorial doesnot. Certificates are easier to use, can be revoked and are less hassle thanmanaging usernames and passwords.
On Android with the StrongSwan Application you can just import the .p12 we aregoing to create later on. OS X and iOS from 10.10 and 9 upwards also supportthis authentication method.
You might want to install haveged to speed up the key generation process:
Haveged provides a constant source of entropy and randomness.
Start by creating a self singed root CA private key:
Generate a self signed root CA certificate of that private key:
You can view the certificate properties with the following command:
Example output:
Generate the VPN Host key. This is the keypair the VPN server host will use toauthenticate itself to clients. First the private key:
Generate the public key and use our earlier created root ca to sign the publickey:
The domain name or IP address of your VPN server, which is later entered in theclients connection properties, MUST be contained either in the subjectDistinguished Name (CN) and/or in a subject Alternative Name (--san). If thisdoes not match the clients will fail to connect.
The built in Windows 7 VPN client needs the serverAuth extended key usage flagin your host certificate as shown above, or the client will refuse to connect.In addition, OS X 10.7.3 or older requires the ikeIntermediate flag, which wealso add here.
We add the IP address twice, one with an @ in front so that it gets added asan subjectAltName of the DNSName type and one of the IPAddess type.
Let's view the certificate:
Output:
You can also use OpenSSL to see the contents, here is an excerpt:
Output:
The private key (/etc/ipsec.d/private/strongswanKey.der) of the CA should bemoved somewhere safe, possibly to a special signing host without access to theInternet. Theft of this master signing key would completely compromise yourpublic key infrastructure. Use it only to generate client certificates whenneeded.
This key needs to be added into /etc/ipsec.secrets, otherwise StrongSwan willnot use it.
Add the key:
The format : RSA keyname is important, don't forget the space. You can checkafterwards if StrongSwan has the private key available with the ipseclistcerts command:
Output:
If it doesn't say has private key on the pubkey line your filename or syntaxis wrong.
Client certificate
Any client will require a personal certificate in order to use the VPN. Theprocess is analogous to generating a host certificate, except that we identify aclient certificate by the clients e-mail address rather than a hostname.
We create a keypair for the example user 'John'.
Ubuntu L2tp Ipsec
Private key:
Public key, signed by our root ca we generated:
A VPN client needs a client certificate, its corresponding private key, and thesigning CA certificate. The most convenient way is to put everything in a singlesigned PKCS#12 file and export it with a paraphrase.
Convert the required keys to PEM formt before converting to a .p12:
Construct the .p12:
Enter a passphrase twice, then you have a .p12. You can send John.p12 and itsexport paraphrase to the person who is going to install it onto the client. Insome cases (iOS for example) you have to separately include the CA certificatecacerts/strongswanCert.pem.
Transport this John.p12 file and the password over seperate channels to aclient.
If you need any more user certificates, repeat the above steps with other userdata. You can also do this later on.
Revoking a certificate
If a certificate is lost or stolen, it must be revoked so nobody can use it toconnect to your VPN server. Assuming the certificate from the previous step gotstolen, we revoke it with:
Restart ipsec afterwards:
This generates the new certificate revocation list (CRL) crls/crl.der. Whensomeone tries to authenticate with the stolen certificate, he'll receive anauthentication credentials error message, and your log file will containsomething like:
To add another revoked certificate to the same list, we need to copy theexisting list into a temporary file:
Restart ipsec afterwards:
IPSEC Configuration
The main ipsec configuration file is located in /etc/. We are going to editit:
Place the following contents:
The configuration has settings for IKEv2 + RSA certificates. This is, as statedabove, the most secure method. Older tutorials also set up IKEv1 (xauth) andusername-password combo, but that is considered insecure.
Apple added support for IKEv2 in iOS 8, but it needs to be configured using acustom configuration profile. OS X 10.9 and lower do not support IKEv2.
Beginning with iOS 9, IKEv2 connections are natively supported. However, iOS9only supports the use of certificates or username/password, but not both.
For iOS 9+ and OS X 10.10+ you need to make sure the leftid= is the same asthe CN in your certificate. You also need to enter that on the devices,otherwise you'll get a no matching peer config found log error.
Android 4+ and Windows 7+ support IKEv2.
Clients will get the Google DNS servers and an IP address in the 10.42.42.0/24range. We use a strong ciphersuite.
The leftcert=vpnHostCert.der expands to the path/etc/ipsec.d/certs/vpnHostCert.der.
Firewall & Packet Routing
Configure the iptables firewall to allow vpn traffic and to forward packets:
Replace %SERVERIP% with the external IP of the VPN server. If your externalinterface is not named ethX (+ is a wildcard) then rename appropriately.
Execute the below commands to enable kernel IP packet forwarding and disable ICPredirects.
Set these settings for other network interfaces:
Apply them:
Persistent settings via /etc/rc.local
To make sure this keeps working at boot you might want to add the following to/etc/rc.local:
Add it before the exit 0 line and replace %SERVERIP% with the external IP ofyour server.
Start the VPN
All the configuration on the server is now done. Enable the VPN at startup:
And start it:
If you get a permission denied error, stroke the files with apparmor:
Check the status of the service:
Output:
And a more elaborate status:
Output:
Client Configuration
Ubuntu 18.04 Cisco Ipsec Vpn
See the Strongswan Wiki for guides on configuring Windows and OS X/iOSclients
On Android, the easiest way is to install the StrongSwan app, copy overthe .p12 and connect with the IP and option IKEv2 Certificate. Nothing more:
Just one tap to Connect and you're good to go:
Sources
Thanks to:
- StrongSwan Wiki and the
- StrongSwan ipsec.conf reference for most of the configuration.
- zeitgeist for the certificate setup.
Ubuntu Cisco Ipsec Vpn Client
